Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
An overview of the BigQuery integration with Seda
There are three steps to connect Big Query with Seda:
Enable the Big Query API
Create a service account for Seda
Connect Big Query to Seda
From the Navigation panel on the left, go to IAM & admin > Service accounts
Click Create Service Account along the top
Enter a name (for example: “seda”) and click Create
When assigning permissions, make sure to grant the following permissions:
a) If you're creating the service account via the GCP console add the following roles:
b) If you're programatically creating the service account add the following roles:
Log into your Seda profile
From the Navigation panel on the left go Integrations > Add new integration
Select Big Query
Enter in the project name and paste the JSON key file contents that was downloaded
Click "Connect"
Log in to your existing project on GCP and . Once you’ve done so, you should see BigQuery in the of Cloud Platform.
To provide to Seda for extracting Big Query metadata, you can create a new service account following the steps below. Refer to for more information.
5. . The downloaded file will be used to create your warehouse in the next section.
Customize and manage your integration after setup.
On the Integrations page, you can easily view and search through all your integrations. You can see details about your integrations including the last and upcoming runs, as well as the status of the most recent run. Additionally, you can use the command palette to run or delete multiple integrations at once.
Deleting an integration from the workspace will remove all associated resources.
If you click into an integration, the following options become available.
After selecting an integration, you'll find the Enabled toggle in the top right corner. By default, all integrations are enabled. If toggled off, the integration is paused, meaning it will not run automatically based on the schedule set.
In the top right corner, you'll also see the Run Sync button. This action triggers a manual sync. Clicking this button allows you to choose whether the sync should Pull or Push metadata.
This is the first page you’ll see when you navigate to an integration. It provides a detailed history of past syncs, allowing you to review each sync's stages, the number of resources pulled, and any errors that may have occurred.
If applicable to the integration, use this page to select which Groups or Schemas you want to sync. Click the Refresh button to check for any new Groups or Schemas available for import. By default, all Groups and Schemas will be selected and included in the sync. If you'd like to change this default behaviour, navigate to the integrations page and change the schemas imported to Seda.
When setting up integrations in Seda, you may notice that some settings pages or references mention "Secoda" instead of "Seda." This is expected and not a cause for alarm. Since Seda shares some architecture with Secoda's platform and is maintained by the same company, some integration components and backend systems use the same framework. These references to Secoda simply reflect the shared infrastructure between the two platforms and do not impact the functionality or security of your Seda implementation
Welcome to Seda! Seda is an AI-powered data assistant designed to help you efficiently search, analyze, and manage your data across various platforms.
Seda is a specialized AI tool that connects directly to your data sources, allowing you to interact with your data using natural language. Unlike general-purpose chatbots, Seda provides context-rich responses by retrieving actual insights from your connected data sources. This makes it easier to find information, write queries, document processes, and visualize data without needing to switch between multiple tools.
Seda is managed and maintained by Secoda and shares some architecture with Secoda. Secoda is a company that has worked with hundreds of organizations and maintained a SOC2 certification for 4 years, graduated from YCombinator, and raised over $15M of funding to date. This institutional backing ensures Seda is a reliable, secure, and continuously improving solution for your data needs.
Seda supports integrations with a variety of data sources, including databases, data warehouses, and productivity tools. Some of the supported integrations are:
Databases: MySQL, PostgreSQL, Microsoft SQL Server
Data Warehouses: Snowflake, BigQuery, Redshift.
Transformation tools: dbt cloud and Core
Productivity Tools: Confluence, Jira, Google Drive, Confluence etc.
To connect a data source:
Navigate to the Integrations page in your Seda workspace.
Click on "Add Integration."
Select the desired data source from the list.
Provide the necessary credentials and configuration details.
Click "Connect" to establish the integration.
Once your data sources are connected, Seda can synchronize metadata and usage statistics to keep your information up-to-date. You can configure sync schedules as follows:
Scheduled Syncs: Set to run on a daily, weekly, or monthly basis.
Manual Syncs: Admins can initiate one-off syncs at any time for immediate updates.
Regular syncing ensures that search results and popularity metrics reflect the most current data usage.
To automate your syncs, use this page to set the run frequency with a Cron Expression. You can learn more about Cron Expressions . If you don’t specify a schedule, the default is 0 0 * * *, which runs the sync daily at midnight UTC.
Welcome to Seda! Seda is an AI-powered data assistant designed to help you efficiently search, analyze, and manage your data across various platforms. This guide will walk you through the initial steps to set up and start using Seda effectively.
To get started, visit and sign up for a free account. The free plan includes access to 5 daily chats and unlimited integrations. If you require more features and flexibility, consider upgrading to the Pro plan for $20 per month, which offers unlimited chats and additional capabilities.
For specific instructions on integrating with each data source, refer to the of the Seda Docs.
An overview of the Redshift integration with Seda
There are three steps to connect Redshift with Secoda:
Create a database user
Connect Redshift to Secoda
Whitelist Secoda IP Address
When connecting to Redshift in Secoda, use the username/password you’ve created here instead of your admin account.
After creating a Redshift warehouse, the next step is to connect Secoda:
In the Secoda App, select ‘Add Integration’ on the Integrations tab
Search for and select ‘Redshift’
Enter your Redshift credentials
Click 'Connect'
Redshift clusters can either be in a EC2 Classic subnet or VPC subnet.
Navigate to your Redshift Cluster settings: Redshift Dashboard > Clusters > Select Your Cluster
Click on the Cluster Security Groups
Open the Cluster Security Group
Click on “Add Connection Type”
Navigate to your Redshift Dashboard > Clusters > Select Your Cluster
Click on the VPC Security Groups
Select the “Inbound” tab and then “Edit”
Navigate back to your Redshift Cluster Settings: Redshift Dashboard > Clusters > Select Your Cluster
Select the “Cluster” button and then “Modify”
Make sure the “Publicly Accessible” option is set to “Yes”
The username and password you’ve already created for your cluster is your admin password, which you should keep for your own usage. For Secoda, and any other 3rd-parties, it is best to create distinct users. This will allow you to isolate queries from one another using and perform audits easier.
To create a , you’ll need to log into the Redshift database directly and run the following SQL commands:
Secoda only uses the system tables for our metadata extraction, the extraction query can be viewed .
VPCs keep servers inaccessible to traffic from the internet. With VPC, you’re able to designate specific web servers access to your servers. In this case, you will be whitelisting the to read from your data warehouse.
If your cluster has a field called Cluster Security Groups, proceed to
Or if your cluster has a field called VPC Security Groups, proceed to
Choose Connection Type CIDR/IP and authorize the to read into your Redshift Port
Allow Secoda to read into your Redshift Port using the .
You can find more information on that .
List of all the metadata that Seda pulls from to Redshift
Seda pulls the following metadata from Redshift:
Tables
Name
Description
Schema
Database
External Usage (Popularity)
External Updated At
Views
Name
Description
Schema
Database
External Usage (Popularity)
External Updated At
Columns
Name
Description
Type
Foreign Key
Primary Key
Column Profile
Min
Max
Median
STD Deviation
Value Distribution
Statistic Value Count
Percent Filled
Unique
Creation Query
Common Queries
Lineage
Redshift Column <-> Redshift Column
Redshift View <-> Redshift View
Redshift Table <-> Redshift Table
Redshift Table <-> Redshift View
Redshift Table <-> Dashboards from other sources
Redshift Table <-> Tables from other sources
Redshift Table, Views <-> Jobs from other sources
Preview of first 50 rows (Optional)
List of all the metadata that Seda pulls from MySQL
Seda pulls the following metadata from MySQL:
Tables and Views
Name
Description
Schema
Database
Columns
Name
Description
Type
Sort Order
Foreign Key
Primary Key
Column Profile
Min
Max
Median
STD Deviation
Value Distribution
Statistic Value Count
Percent Filled
Unique
Lineage
MySQL Table <-> My SQL Table
MySQL Column <-> MySQL Column
MySQL Column <-> MySQL View
MySQL Table <-> MySQL Table
MySQL Table/View <-> Tables from other sources
List of all the metadata that Seda pulls pulls from BigQuery
Seda pulls the following metadata from BigQuery:
Tables/Views
Name
Description
Last Updated Timestamp
Schema
Database
Frequent users
Policy tags
Labels
Fields (Fields are referred to as Columns in Seda)
Name
Description
Type
Foreign Key
Primary Key
Policy tags
Labels
Column Profile
Min
Max
Median
STD Deviation
Value Distribution
Statistic Value Count
Percent Filled
Unique
Queries (Popularity)
Lineage
BQ Column <-> BQ Column
BQ Table <-> BQ Table
BQ Column <-> BQ View
BQ Table <-> Tables from other sources
This page walks through the current integrations that Secoda supports and what's on the roadmap.
Secoda currently integrates with many different tools, see below for the types of tools we integrate with and instructions around how to set up the integration in your Secoda workspace.
An overview of the Postgres integration with Seda
There are three steps to connect Postgres with Postgres:
Create a database user
Connect Postgres to Seda
Whitelist Seda IP Address
The username and password you’ve already created for your cluster is your admin password, which you should keep for your own usage. For Seda, and any other 3rd-parties, it is best to create distinct users.
To create a new user, you’ll need to log into the Postgres database directly and run the following SQL commands:
When connecting to Postgres in Seda, use the username/password you’ve created here instead of your admin account.
After creating a Postgres user, the next step is to connect Seda:
In the Seda App, select ‘Add Integration’ on the Integrations tab
Search for and select ‘Postgres’
Enter your Postgres credentials
Click 'Connect'
VPCs keep servers inaccessible to traffic from the internet. With VPC, you’re able to designate specific web servers access to your servers. In this case, you will be whitelisting the Seda IPs to read from your data warehouse.
There are three steps to get started using dbt with Seda:
Retrieve your Account ID
Retrieve a Service Token
Connect dbt to Seda
You can determine your account ID by going to the Account Settings page of dbt Cloud console. In the URL, for example in the URL below, the account ID is 12345 https://cloud.getdbt.com/settings/accounts/12345/pages/projects
Seda uses the dbt Cloud REST API, which is only available paying dbt Cloud customers. For Seda to retrieve metadata from dbt, you need to generate a Service Token with. To do this, go to Account Settings > Service Tokens and click "New Token".
The minimum permissions are Analyst of the selected projects for the Service Account. Once the projects have been selected Save the token and copy the generated token.
After enabling the dbt REST API, the next step is to connect Seda:
In the Seda App, select Add Integration on the Integrations tab
Search for and select the dbt Cloud integration
Enter your dbt account ID and Service Token. This information is kept encrypted.
Click Connect
Not using Secoda to manage your data documentation yet? Sign up for free 👈
Allow Seda to read into your Postgres database using the .
An overview of the Snowflake integration with Seda
There are four steps to connect Snowflake with Seda.
Create Role for Seda
Create User for Seda
Connect Snowflake to Seda in the Seda UI
You must be either an ACCOUNTADMIN, or have MANAGE GRANTS privileges in order to run the commands necessary to connect.
We recommend naming the User, Role, and Warehouse, SEDA_USER, SEDA_ROLE, SEDA_WAREHOUSE respectively. However, naming them this way is not necessary to integrate.
Navigate to Worksheets, select a database, and run the following commands in that database. You'll need to run these commands for all of the databases that you'd like Seda to import metadata from.
[Optional] If you are using Snowflake Dynamic Tables, to bring in those tables, you have to grant MONITOR permissions to the SECODA role on all of those tables.
This step has to be repeated for every single dynamic table that you wish to bring into Seda.
If you would like you use key-pair authentication instead of a password you will need to:
Take the final key and convert it to base64 encoding. You can run the following command to convert the key.
In the Seda App, select Add Integration on the Integrations page. Search for and select “Snowflake”.
Add your credentials as follows:
User - The name of the User created in Step 2.
Password - The Password set in Step 2.
Alternatively you can select the key-pair authentication and enter the private key and passphrase created in step 2.
Account - This is the Account ID of your cluster.
Warehouse - The Warehouse set in Step 1.
The account ID will likely be the business name, as well as the cloud region, if Snowflake is cloud hosted. See below for some examples.
URL: https://secoda.snowflakecomputing.com
ACCOUNT ID: secoda
URL: https://secoda.us-east-1.snowflakecomputing.com
ACCOUNT ID: secoda.us-east-1
URL: https://secoda.west-europe.azure.snowflakecomputing.com
ACCOUNT ID: secoda.west-europe.azure
Snowflake has made some recent changes where URLs can be different than the standard format above. In these cases, you can find the correct account id by:
Clicking on the account selector in Snowflake
This should create a URL ending with snowflakecomputing.comand you can follow the steps abvoe to determine the account id.
In order to resolve this error, please run the following command:
GRANT imported privileges on database SNOWFLAKE to ROLE SECODA;
This error could be the result of an incorrect Account ID. Please double check that your Account ID is properly added.
No active warehouse selected in the current session
This error can be due to the warehouse name not being fully uppercase. Updating the warehouse name to all uppercase letters should resolve this issue.
Whitelist
. Once the key is created, you can run the following command to connect the key to the SECODA_USER.
If you create a network policy with Snowflake, add the following to the “Allowed IP Addresses” list.
You can find the Account ID in the Snowflake URL. The account ID is usually a substring of the URL, before snowflakecomputing.com. If your Snowflake URL does not contain snowflakecomputing.com, see to determine your Account ID.
Hovering over the specific account you want to connect to \
Then clicking the copy account URL button on the 3rd section that shows the accounts details (organization id,
List of all the metadata that Seda pulls from Snowflake
Seda pulls the following metadata from Snowflake:
Tables
Name
Description
Last Updated Timestamp
External Usage (Popularity)
Schema
Database
Frequent Users
Tags
Views
Name
Description
Last Updated Timestamp
External Usage
Schema
Database
Frequent Users
Tags
Columns
Name
Description
Type
Foreign Key
Primary Key
Tags
Column Profile
Min
Max
Median
STD Deviation
Value distribution
Statistic Value Count
Percent Filled
Unique
Creation Query
Common Queries
Lineage
Snowflake Column <-> Snowflake Column
Snowflake Table <-> Snowflake Table
Snowflake Column <-> Snowflake View
Snowflake Table <-> Snowflake View
List of all the metadata that Seda pulls from Confluence
dbt is a secondary integration that adds additional metadata on to your data warehouse or relational database tables. Before connecting dbt make sure to connect a data warehouse or relational database first. These include Snowflake, BigQuery, Postgres, Redshift, etc.
There are several options to connect dbt core with Seda:
(Recommended) Connect an AWS, GCP, or Azure storage bucket/container
Upload a manifest.json and run_results.json through the UI
Upload a manifest.json and run_results.json through the API
This option is recommended to ensure that Seda always has the latest manifest.json and run_results.json files from dbt Core. Seda will only sync these files from the bucket.
You can connect to the AWS S3 bucket using an AWS IAM user, or AWS Roles.
Login to GCP cloud console.
Create a service account.
Grant access to the service account from the Bucket page as “Storage Object Viewer”.
Turn on interoperability on the bucket. Generate HMAC keys for a service account with read access to the bucket. Both located here:
Setup CORS. GCP requires this be done over CLI. Like the following:
Copy
cors.json
Copy
Save the HMAC keys to be used in the connection form.
Access Key Id
Secret
Region bucket region for GCP
S3 Endpoint must be added and set to https://storage.googleapis.com
Connect your S3 bucket to Seda
Choose the Access Key tab and add the HMAC keys saved above to the relevant fields.
Test the Connection - if successful you'll be prompted to run your initial sync
Go to portal.azure.com and then click Storage accounts.
Copy the name of the desired storage account. Enter that in the integration form.
Click on your storage account and under Security + networking select Access keys.
Copy the Connection string and add to your integration form.
Test the connection.
The dbt manifest file contains complete information about how tables are transformed and how they are connected in terms of data lineage. It details the model to table relationships, providing a complete and accurate lineage view.
This is a one time sync with your manifest.json file. You can upload the file following these steps:
Choose the File Upload tab and select your manifest.json and run_results.json files using the file select
Test the Connection - if successful you'll be prompted to run your initial sync
4. Now that a sync has been triggered, you can now monitor your sync in the UI!
Navigate to and click dbt Core
Navigate to and click dbt Core
An overview of the MySQL integration with Seda
There are three steps to get started using MySQL with Seda:
Create a database user
Connect MySQL to Seda
Whitelist Seda IP Address
The username and password you’ve already created for your cluster is your admin password, which you should keep for your own usage. For Seda, and any other 3rd-parties, it is best to create distinct users.
To create a new user, you’ll need to log into the MySQL database directly and run the following SQL commands:
When connecting to MySQL in Seda, use the username/password you’ve created here instead of your admin account.
After creating a MySQL user, the next step is to connect Seda:
In the Seda App, select ‘Add Integration’ on the Integrations tab
Search for and select "MySQL"
Enter your MySQL credentials
Click 'Connect'
VPCs keep servers inaccessible to traffic from the internet. With VPC, you’re able to designate specific web servers access to your servers. In this case, you will be whitelisting the Seda IPs to read from your data warehouse.
An overview of the Confluence integration with Seda
There are 3 steps to connect Confluence with Seda:
Create an API token and retrieve the email used to create it
Retrieve your domain name
Connect Confluence to Seda
Once logged in, follow these steps to create a token:
Click on the profile icon in the top right
Click on ‘Manage Account’
Ensure you are on the ‘Profile and visibility’ tab
Scroll to the bottom to retrieve the email address being used
Select the ‘Security’ tab at the top of the page
Select the ‘Create API token’ button and give it a label
Copy and save the API token, as it can’t be accessed again
The domain name is the name given to the Confluence workspace containing spaces. The name can be found in the URL when in the confluence workspace, in the format of https://{domain-name}.atlassian.net/. For example, the url could be "https://seda.atlassian.net/wiki/home", so the domain name would be Seda.
After retrieving the API token and domain name, the next step is to connect to Seda:
In the Seda App, select ‘Add Integration’ on the Integrations tab
Search for and select Confluence
Enter your Confluence domain name, email address and API token retrieved above
Once successfully connected, a prompt labeled Schema will appear which corresponds to Confluence spaces. Select the spaces you want to integrate into Seda
Run the initial extraction
Any spaces that are created or deleted will not be updated under the spaces tab on the integration page. Any new public spaces created will be automatically imported during the next sync, and any deleted space contents will be removed. If you do not want any new spaces brought in, then the confluence integration must be deleted and re-connected for the space options to be updated.
Allow Seda to read into your MySQL database using the .
API tokens in Confluence are based on individual accounts, so with an account that has access to the spaces desired.
Select the ‘’ link under the API token subtitle
The domain name can also be retrieved from the page, under the Confluence image.
List of all the metadata that Seda pulls from Postgres
Seda pulls the following metadata from Postgres:
Tables and Views
Name
Description
Last Updated Timestamp
Schema
Database
View Definition (Table Creation Query)
Columns
Name
Description
Type
Foreign Key
Primary Key
Column Profile
Min
Max
Median
STD Deviation
Value Distribution
Statistic Value Count
Percent Filled
Unique
Lineage
Postgres Table <-> Postgres Table
Postgres View <-> Postgres Table
Postgres View <-> Postgres Column
Postgres Column <-> Postgres Column
Postgres Table/View <-> Tables from other sources
Postgres Table/View <-> Dashboards from other sources
Postgres Table/View <-> Jobs from other sources
Key questions about the Secoda product
Wondering if the Seda AI is the right tool for your workspace considering your data governance and privacy policies?
Ensuring our customers feel safe and comfortable using this tool is a top priority for us. Read on to learn how we are ensuring your data is safe and secure.
The only data sent to the LLM provider is the metadata in your workspace. Metadata is defined as properties and documentation describing your resources, including Owners, Tags, Descriptions, Definitions, Popularity, Resource Names, and more. The data within the resource does not leave the workspace.
No, all metadata is specific to your workspace and is not shared or accessible by anyone who isn't granted access to your workspace. You cannot ask Secoda AI about metadata that is not in your workspace.
To improve your user experience with Seda AI, your prompts are saved. You can see your previous prompts in the right hand side panel in the Seda AI page.
Anthropic is GDPR compliant and take data privacy very seriously. They have implemented measures to ensure compliance with GDPR and other data privacy laws, such as providing users with the ability to delete their data and implementing data protection impact assessments. Secoda Inc, which manages Seda is SOC2 complaint and also takes security seriously.
Anthropic hosts their servers hosted strictly in the US, so all metadata that is sent to the LLM provider is sent to the US.
Our AI strictly adheres to schema-based data access permissions. If you don't want certain data in Seda, you can remove it from the sync during the integration step.
In Seda, the Popularity of a resource is a piece of metadata pulled directly from the source. It is defined as the number of queries (for a database/data warehouse) or the number of views (for a data visualization tool) over the previous 24 hours from the last sync with that source. When ranking search results by Popularity, Seda uses a combination of external and internal metrics.
Search results are based on a number of factors. The primary factor is the matching of text in the resource title or description to what has been inputted into the search bar. Popularity of the resource (from external and internal metrics) are also used to order the search results.
You can choose when to run an extraction for each integrations. Schedules for syncs can be set to run on a daily, weekly, or monthly basis. One off manual syncs are available as well, and can only be run by Admins.
Seda prioritizes data security by requiring the creation of dedicated database users with specific permissions and the whitelisting of Seda's IP addresses. This approach ensures that Seda accesses only the necessary metadata without compromising the security of your data sources .
According to Anthropic, any data sent over through the API is not used to train their Large Language Model. You can read more about Anthropic's policies .
Everything you need to know about Secoda's policies
See all policies at https://trust.secoda.co
Not using Secoda to manage your data documentation yet? Sign up for free 👈
This page walks through connecting your data sources via a direct SSH tunnel
There are three main steps to set up a tunnel:
Add the Public Key to the authorized_keys file in your host.
Create an EC2 instance from the AWS Management Console in a public subnet in the same VPC as the resource that you'd like to integrate with Secoda.
Add the SSH key from Secoda.
Create a Security Group for this instance, and add an inbound rule for the Secoda IPs.
Make sure the EC2 instance has access to the resource that you'd like to integrate with Secoda. This might mean adding an inbound rule for the IP of the EC2 instance to the database or source that you're integrating with Secoda.
Create a Virtual Network from the Azure console, that has access to the database or datasource that you'd like to integrate with Secoda. Make sure the Azure firewall is enabled for this network.
Create a Virtual Machine. This machine is acting as the jump server. This VM does not need an public access, but must have access to the database or datastore that is meant to integrate with Secoda.
Go to your firewall rules, and add a NAT rule.
Protocol should be set to TCP
Destination IP address should be the IP address of your Firewall
Default Port is 22
Translated IP address should be the IP address of the Virtual Machine
From within your instance, you'll need to create a user and set up the SSH key provided by Secoda. The follow commands are recommended to do this:
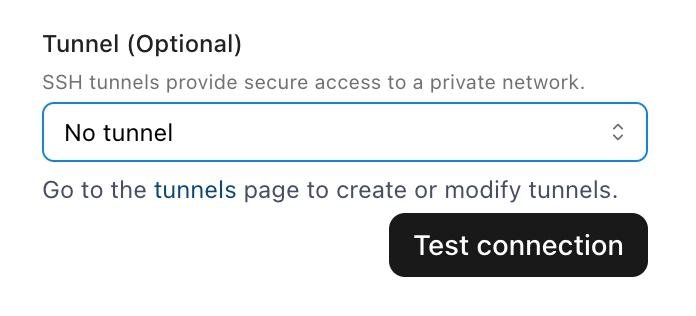
Once your tunnel has been made, navigate to the source that you're integrating with. On the connect page, add the credentials for the datasource.
At the bottom of the connect page, you'll see the option to add a tunnel. Click on the arrow to see a drop down menu with your recently created Tunnel. Select this tunnel, and click Test Connection to complete your integration setup!
If you're having trouble establishing a connection with a standard tunnel, check the following:
Whitelist the Secoda IP Ensure that the Secoda IP is whitelisted on your Bastion host.
Verify the Public Key
Confirm that the public key provided during tunnel creation is correctly added to the ~/.ssh/authorized_keys file of the user on the Bastion host.
Check Permissions on SSH Files Ensure that the permissions on SSH-related files and directories are set correctly:
~/.ssh directory: 0700
~/.ssh/authorized_keys file: 0600
Note: The permissions for authorized_keys should be 0600 (not 0644) to maintain strict security compliance.
Test Network Connectivity
Verify that the Bastion host can connect to your data source. Replace $data_source_host and $data_source_port with the actual hostname and port of your data source.
Check that you can use the bastion host from your personal machine. You will need to use your own private and public keys, not the public key from the above step. Replace the values where appropriate.
Tunnels require you to run an SSH server process () on a host accessible from the public internet. These hosts are often referred to as jump hosts or Bastion hosts and can be set up in nearly all cloud providers. The sole purpose of these host is to provide access to resources in a private network from an external network like the internet.
Configure a host in your environment that is accessible from the public internet. Make sure the is whitelisted.
and add in the configuration details from the host (SSH Username, SSH Hostname, Port). Once you submit these details, a Public Key will be shown.
Source IP address should be set to the
This page walks through connecting your data sources via a Reverse SSH Tunnel
The Reverse SSH Tunnel is used securely connect local data sources without opening ports, while encrypting data in-transit.
On your own EC2/VM, you will run the secoda/agent docker image. You can use docker-compose, like so:
Copy the details to your clipboard, and replace the contents of your docker compose file with this configuration.
Once you have inputted the values, you can restart the Secoda Agent with:
On an integration credentials page, fill in the integration connection details. DNS names are resolved on the agent, so you may use local hostnames.
Select the reverse tunnel you would like to use. Test connection.
Upon running the agent, if the agent becomes stuck on the version number during the startup process, similar to:
This typically means that the outbound connection is blocked. Please check your firewall settings. Secoda can adjust the outbound port to a whitelisted one if necessary.
To retrieve the docker compose environment for your tunnel, go to and create a new reverse tunnel.
Secoda is committed to security and focused on keeping you and your data safe.
Secoda is committed to security and focused on keeping you and your data safe. Secoda adheres to industry-leading standards while connecting and loading data from all of your data sources.
Contact [email protected] if you have any questions or comments.
All connections to Secoda's web portal are encrypted by default using industry-standard cryptographic protocols (TLS 1.2+).
Any attempt to connect over an unencrypted channel (HTTP) is redirected to an encrypted channel (HTTPS).
To take advantage of HTTPS, your browser must support encryption protection (all versions of Google Chrome, Firefox, and Safari).
Databases and API cloud applications - Secoda only requires READ permissions. For data sources that by default grant permissions beyond read-only, Secoda will never make use of those permissions.
All customer data, besides what is listed below, is removed from Secoda's system within 24 hours using object lifecycle management. Secoda retains subsets of a customer's data that are required to provide and maintain Secoda's solution. This includes only:
Customer access credentials - Secoda retains customer database credentials and SaaS OAuth tokens in order to securely and continuously extract data and troubleshoot customer issues. These credentials are stored securely using industry standard encryption.
Customer metadata - Secoda retains metadata such as table and column names for each integration so that this information can be shown to your organization in Secoda' user interface.
Since Secoda relies on AWS, physical and environmental security is handled entirely by Amazon. Amazon provides an extensive list of compliance and regulatory assurances, including SOC 1/2-3, PCI-DSS and ISO27001.
Users can use Single Sign-On through Google or Microsoft Apps.
Only users of your organization registered within Secoda and Secoda operations staff have access to your organization's Secoda workspace.
Your organization's Secoda workspace provides visibility into the status of each integration, the aforementioned metadata for each integration, and the ability to pause or delete the integration connection - not organization data.
Organization administrators can request that Secoda revoke an organization member's access at any point; these requests will be honored within 24 hours or less.
Organizations administrators can request that Secoda delete all organizations metadata at any point; these requests will be honoured without 24 hours or less.
Secoda requires that all employees comply with security policies designed to keep any and all customer information safe, and address multiple security compliance standards, rules and regulations.
Security policies and procedures are documented and reviewed on a regular basis.
Current and future development follows industry-standard secure coding guidelines, such as those recommended by OWASP.
Networks are strictly segregated according to security level. Modern, restrictive firewalls protect all connections between networks.
Secoda currently has SOC 2 compliance and can provide documentation upon request.
To date, Secoda has not experienced a breach in security of any kind. In the event of such an occurrence, Secoda protocol is such that customers would be made aware as soon as the compromise is confirmed.
At Secoda, we are committed to keeping our systems, data and product(s) secure. Despite the measures we take, security vulnerabilities will always be possible.
If you believe you’ve found a security vulnerability, please send it to us by emailing [email protected]. Please include the following details with your report:
Description of the location and potential impact of the vulnerability
A detailed description of the steps required to reproduce the vulnerability (POC scripts, screenshots, and compressed screen captures are all helpful to us)
Please make a good faith effort to avoid privacy violations as well as destruction, interruption or segregation of services and/or data. We will respond to your report within 5 business days of receipt and will attempt to keep you regularly informed of our progress toward resolving the vulnerability. If you have followed the above instructions, we will not take any legal action against you regarding the report.
IMPORTANT: Secoda cannot access your data without your approval.
When working on a support ticket, we may need to access your data to troubleshoot or fix your broken connector or destination. In that case, we will ask you to grant Secoda access to your data for the next 21 days. You can allow or deny data access. If you grant us data access, you can revoke it at any moment before the 21-day diagnostic period has expired.
The privacy policy that Seda uses
We at Secoda (“Company,” “we,” “us,” “our”) know you care about how your personal information is used and shared, and we take your privacy seriously. Please read the following to learn more about our Privacy Policy.
By using or accessing our products, services or website (collectively, “Services”) in any manner, you acknowledge that you accept the practices and policies outlined in this Privacy Policy, and you hereby consent that we will collect, use, and share your information in the following ways.
Remember that your use of Company’s Services is at all times subject to the Terms and Conditions, which incorporates this Privacy Policy. Any terms we use in this Policy without defining them have the definitions given to them in the Terms and Conditions.
What does this Privacy Policy cover?
This Privacy Policy covers our treatment of personally identifiable information ("Personal Information") that we gather when you are accessing or using our Services, but not to the practices of companies we don’t own or control, or people that we don’t manage. We gather various types of Personal Information from our users, as explained in more detail below, and we use this Personal Information internally in connection with our Services, including to personalize, provide, and improve our services, to allow you to set up a user account and profile, to contact you and allow other users to contact you, to fulfill your requests for certain products and services, and to analyze how you use the Services. In certain cases, we may also share some Personal Information with third parties, but only as described below.
Will Company ever change this Privacy Policy?
We’re constantly trying to improve our Services, so we may need to change this Privacy Policy from time to time as well, but we will alert you to changes by placing a notice on seda.ai , by sending you an email, and/or by some other means. Please note that if you’ve opted not to receive legal notice emails from us (or you haven’t provided us with your email address), those legal notices will still govern your use of the Services, and you are still responsible for reading and understanding them. If you use the Services after any changes to the Privacy Policy have been posted, that means you agree to all of the changes.
What Information does the Company Collect?
Information You Provide to Us:
We receive and store any information you knowingly provide to us. For example, we may collect Personal Information such as your name, email address, phone number. Certain information may be required to register with us or to take advantage of some of our features.
We may communicate with you if you’ve provided us the means to do so. For example, if you’ve given us your email address, we may send you promotional email offers on behalf of other businesses, or email you about your use of the Services. Also, we may receive a confirmation when you open an email from us. This confirmation helps us make our communications with you more interesting and improve our services.
Information Collected Automatically
Whenever you interact with our Services, we automatically receive and record information on our server logs from your browser or device, which may include your IP address, geolocation data, device identification, “cookie” information, the type of browser and/or device you’re using to access our Services, and the page or feature you requested. “Cookies” are identifiers we transfer to your browser or device that allow us to recognize your browser or device and tell us how and when pages and features in our Services are visited and by how many people. You may be able to change the preferences on your browser or device to prevent or limit your device’s acceptance of cookies, but this may prevent you from taking advantage of some of our features.
If you click on a link to a third party website or service, a third party may also transmit cookies to you. Again, this Privacy Policy does not cover the use of cookies by any third parties, and we aren’t responsible for their privacy policies and practices. Please be aware that cookies placed by third parties may continue to track your activities online even after you have left our Services, and those third parties may not honor “Do Not Track” requests you have set using your browser or device.
We may use this data to customize content for you that we think you might like, based on your usage patterns. We may also use it to improve the Services – for example, this data can tell us how often users use a particular feature of the Services, and we can use that knowledge to make the Services interesting to as many users as possible.
Information Collected From Other Websites and Do Not Track Policy
Through cookies we place on your browser or device, we may collect information about your online activity after you leave our Services. Just like any other usage information we collect, this information allows us to improve the Services and customize your online experience, and otherwise as described in this Privacy Policy. Your browser may offer you a “Do Not Track” option, which allows you to signal to operators of websites and web applications and services (including behavioral advertising services) that you do not wish such operators to track certain of your online activities over time and across different websites. Our Services do not support Do Not Track requests at this time, which means that we collect information about your online activity both while you are using the Services and after you leave our Services.
Will Company Share Any of the Personal Information it Receives?
We do not rent or sell your Personal Information in personally identifiable form to anyone. We do not view, sell or collect any data related to our Services that we have not been granted access to. We may share your Personal Information with third parties as described in this section:
Information that’s been de-identified. We may de-identify your Personal Information so that you are not identified as an individual, and provide that information to our partners. We may also provide aggregate usage information to our partners (or allow partners to collect that information from you), who may use such information to understand how often and in what ways people use
our Services, so that they, too, can provide you with an optimal online experience. However, we never disclose aggregate usage or de-identified information to a partner (or allow a partner to collect such information) in a manner that would identify you as an individual person.
Affiliated Businesses: In certain situations, businesses or third party websites we’re affiliated with may sell or provide products or services to you through or in connection with the Services (either alone or jointly with us). You can recognize when an affiliated business is associated with such a transaction or service, and we will share your Personal Information with that affiliated business only to the extent that it is related to such transaction or service. We have no control over the policies and practices of third party websites or businesses as to privacy or anything else, so if you choose to take part in any transaction or service relating to an affiliated website or business, please review all such business’ or websites’ policies.
Agents: We employ other companies and people to perform tasks on our behalf and need to share your information with them to provide products or services to you. Unless we tell you differently, our agents do not have any right to use the Personal Information we share with them beyond what is necessary to assist us.
User Profiles and Submissions: Certain user profile information, including your name, location, and any video or image content that such user has uploaded to the Services, may be displayed to other users to facilitate user interaction within the Services or address your request for our services. Your user name may also be displayed to other users if and when you send messages or comments or upload images or videos through the Services.
Business Transfers: We may choose to buy or sell assets, and may share and/or transfer customer information in connection with the evaluation of and entry into such transactions. Also, if we (or our assets) are acquired, or if we go out of business, enter bankruptcy, or go through some other change of control, Personal Information could be one of the assets transferred to or acquired by a third party.
Protection of Company and Others: We reserve the right to access, read, preserve, and disclose any information that we believe is necessary to comply with law or court order; enforce or apply our Terms and Conditions and other agreements; or protect the rights, property, or safety of Company, our employees, our users, or others.
We seek to protect your Personal Data from unauthorized access, use and disclosure using appropriate physical, technical, organizational and administrative security measures based on the type of Personal Data and how we are processing that data. You should also help protect your data by appropriately selecting and protecting your password and/or other sign-on mechanism; limiting access to your computer or device and browser; and signing off after you have finished accessing your account. Although we work to protect the security of your account and other data that we hold in our records, please be aware that no method of transmitting data over the internet or storing data is completely secure.
We retain Personal Data about you for as long as you have an open account with us or as otherwise necessary to provide you with our Services. In some cases we retain Personal Data for longer, if doing so is necessary to comply with our legal obligations, resolve disputes or collect fees owed, or is otherwise permitted or required by applicable law, rule or regulation. We may further retain information in an anonymous or aggregated form where that information would not identify you personally.\
Is Personal Information about me secure?
Your account is protected by a password for your privacy and security. You must prevent unauthorized access to your account and Personal Information by selecting and protecting your password appropriately and limiting access to your computer or device and browser by signing off after you have finished accessing your account.
We endeavour to protect the privacy of your account and other Personal Information we hold in our records, but unfortunately, we cannot guarantee complete security. Unauthorized entry or use, hardware or software failure, and other factors, may compromise the security of user information at any time.
What Personal Information can I access?
You may access, and, in some cases, edit or delete the following information you’ve provided to us:
name
email address
The information you can view, update, and delete may change as the Services change. If you have any questions about viewing or updating information we have on file about you, please contact us at [email protected]
What choices do I have?
You can always opt not to disclose information to us, but keep in mind some information may be needed to register with us or to take advantage of some of our features.
You may be able to add, update, or delete information as explained above. When you update information, however, we may maintain a copy of the unrevised information in our records. You may request deletion of your account or information by sending a request to [email protected]. Some information may remain in our records after your deletion of such information from your account. We may use any aggregated data derived from or incorporating your Personal Information after you update or delete it, but not in a manner that would identify you personally.
Seda does not sell or rent any of your personal information to third parties including that of minors under the age of sixteen (16). While Seda does not consider the use of advertising cookies on our site as a sale, you have the right to opt out of it.
What if I have questions about this policy?
If you have any questions or concerns regarding our privacy policies, please send us a detailed message to [email protected], and we will try to resolve your concerns.
This Data Processing Addendum (“DPA”) is made as of the Effective Date by and between Secoda, Inc. (“Vendor”), and Customer, pursuant to the Software as a Service Agreement or other written or electronic agreement between the parties (as applicable) (“Agreement“).
This DPA forms part of the Agreement and sets out the terms that apply when Personal Data is processed by Vendor as a Processor under the Agreement. The purpose of the DPA is to ensure such processing is conducted in accordance with applicable laws and with due respect for the rights and freedoms of individuals whose Personal Data are processed. Capitalized terms used but not defined in this DPA have the same meanings as set out in the Agreement.
For the purposes of this DPA:
“Affiliate” means any entity controlled by, controlling or under common control by an entity, where “control” means ownership of or the right to control greater than 50% of the voting securities of such entity.
“Applicable Data Protection Legislation” means as applicable, European Data Protection Legislation and the CCPA.
“CCPA” means the California Consumer Privacy Act of 2018 and any binding regulations promulgated thereunder, in each case, as may be amended from time to time.
“Controller” means the entity which, alone or jointly with others, determines the purposes and means of the processing of Personal Data;
“Customer Data” means Personal Data that the Vendor processes as a Processor on behalf of the Customer.
“Effective Date” means the last date of execution below.
“Europe” means, for the purposes of this DPA, the European Economic Area (which comprises the member states of the European Union, Norway, Iceland and Liechtenstein), the United Kingdom and Switzerland.
“European Data Protection Legislation” means (i) Regulation 2016/679 of the European Parliament and of the Council on the protection of natural persons with regard to the processing of personal data and on the free movement of such data (“GDPR”); and (ii) any applicable data protection laws of the United Kingdom (including the UK GDPR and the Data Protection Act 2018); as may be amended, superseded or replaced from time to time;
“Processor” means an entity that processes Personal Data on behalf of the Controller;
“Personal Data” means “personal data” or “personal information” as defined in and subject to Applicable Data Protection Legislation;
“Standard Contractual Clauses” means the Standard Contractual Clauses for processors as set out in the European Commission’s Decision 2010/97/EU of 5 February 2010, in the form attached as Exhibit C.
“Sub-processor” means any Processor engaged by Vendor or its Affiliates to assist in fulfilling Vendor’s obligations under the Agreement and which processes Customer Data. Sub-processors may include third parties or Vendor Affiliates but shall exclude Vendor employees and consultants.
The terms “personal data”, “controller”, “processor” and “processing” shall have the meaning given to them in European Data Protection Legislation and “process”, “processes” and “processed” shall be interpreted accordingly.
2.1. Applicability. This DPA will apply only to the extent that Vendor processes, on behalf of Customer, Personal Data to which European Data Protection Legislation applies and Personal Data pertaining to California residents.
2.2. Scope. The subject matter of the data processing is the provision of the Services and the processing will be carried out for the duration of the Agreement. Exhibit A sets out the nature and purpose of the processing, the types of Personal Data Vendor processes and the categories of data subjects whose Personal Data is processed.
3.1. Parties’ Roles. To the extent that Vendor processes Customer Data subject to European Data Protection Legislation in the course of providing the Services, it will do so only as a Processor acting on behalf of Customer (as Controller) and in accordance with the requirements of the Agreement.
3.2. Instructions. The Agreement and this DPA set out Customer’s complete documented instructions to Vendor in relation to the processing of Customer Data and any processing required outside of the scope of these instructions will require a prior written agreement between the parties.
3.3. Purpose Limitation. If Vendor is required to process Customer Data for any other purpose by European Union or national law to which Vendor is subject, Vendor shall inform Customer of this requirement before the processing, except where otherwise required by such law.
3.4. Compliance. Customer shall be responsible for ensuring that:
all such notices have been given, and all such authorizations have been obtained, as required under Applicable Data Protection Legislation, for Vendor (and its Affiliates and Sub-processors) to process Customer Data as contemplated by the Agreement and this DPA; it has complied, and will continue to comply, with all applicable laws relating to privacy and data protection, including Applicable Data Protection Legislation; and it has, and will continue to have, the right to transfer, or provide access to, Customer Data to Vendor for processing in accordance with the terms of the Agreement and this DPA.
4.1. Security. The vendor will have in place and maintain throughout the term of this Agreement appropriate technical and organizational measures designed to protect Customer Data against accidental or unlawful destruction or accidental loss, alteration, unauthorized disclosure or access, and against all other unlawful forms of processing (a “Security Incident”). These measures shall at a minimum comply with applicable law and include the measures identified in Exhibit B (“Security Measures“). The customer acknowledges that the Security Measures are subject to technical progress and development and that Vendor may update or modify the Security Measures from time to time, provided that such updates and modifications do not result in the degradation of the overall security of the Services purchased by the Customer.
4.2. Vendor will ensure that any person that it authorizes to process Customer Data (including its staff, agents and subcontractors) shall be subject to a duty of confidentiality (whether a contractual or a statutory duty).
4.3. Upon becoming aware of a Security Incident in respect of Customer Data processed by Vendor on behalf of Customer under this DPA, Vendor shall notify Customer without undue delay and shall provide such information as Customer may reasonably require, including to enable Customer to fulfil its data breach reporting obligations under Applicable Data Protection Legislation. Vendor’s notification of or response to a Security Incident shall not be construed as an acknowledgement by Vendor of any fault or liability with respect to the Security Incident.
4.4 Customer is solely responsible for its use of the Service, including (a) making appropriate use of the Service to ensure a level of security appropriate to the risk in respect of Customer Data; (b) securing the account authentication credentials, systems and devices Customer uses to access the Service; and (c) backing up Customer Data.
5.1. Subprocessing. Customer agrees that (a) Vendor may engage Vendor Affiliates and Sub-processors as necessary and (b) such Affiliates and Sub-processors respectively may engage third party processors to process Customer Data on Vendor’s behalf.
5.2 Vendor shall (i) impose on such Sub-processors data protection obligations that protect Customer Data to the same or substantially similar standard provided for by this DPA, and at a minimum compliant with the requirements of European Data Protection Legislation; and (ii) remain liable for any breach of the DPA caused by a Sub-processor, but only to the same extent that Vendor would be liable if it had provided the services of the Sub-processor directly under the terms of this DPA.
6.1. Location of Processing. Customer understands that effective operation of the Services may require the transfer of Customer Data to Vendor Affiliates or to Vendor’s Sub-processors, such as Amazon Web Services. Customer hereby authorizes the transfer of Customer Data to locations outside Europe, including to Vendor Affiliates and Sub-processors, subject to continued compliance with this Section 6 throughout the duration of the Agreement.
6.2. Transfer mechanism. To the extent Vendor processes (or causes to be processed) Customer Data that is protected by European Data Protection Legislation (“European
Data“) in a country that does not provide an adequate level of protection for Personal Data (within the meaning of applicable European Data Protection Legislation), Vendor agrees to abide by and process such European Data in accordance with the Standard Contractual Clauses, which are incorporated into and form a part of this DPA.
6.3. Alternative transfer arrangements. If Vendor adopts an alternative data export mechanism (including any new version of or successor to the Standard Contractual Clauses adopted pursuant to applicable European Data Protection Legislation) for the transfer of European Data not described in this DPA (“Alternative Transfer Mechanism“), the Alternative Transfer Mechanism shall apply instead of any applicable transfer mechanism described in this DPA (but only to the extent such Alternative Transfer Mechanism complies with applicable European Data Protection Legislation and extends to the territories to which European Data is transferred) and Customer agrees to execute such other and further documents and take such other and further actions as may be reasonably necessary to give legal effect to such Alternative Transfer Mechanism.
6.4.Transfers to the UK. For the avoidance of doubt, when the European Union law ceases to apply to the United Kingdom (“UK“) upon the UK’s withdrawal from the European Union, and until such time as the UK is deemed to provide an adequate level of protection for Personal Data (within the meaning of applicable European Data Protection Legislation), then to the extent Vendor processes (or causes to be processed) any Customer Data protected by European Data Protection Legislation applies to the EEA and Switzerland in the UK, Vendor shall process such Customer Data in compliance with the Standard Contractual Clauses or any applicable Alternative Transfer Mechanism as described above.
6.4. Each party acknowledges that the other party may disclose this DPA (including the Standard Contractual Clauses) and any relevant privacy provisions in the Agreement to the US Department of Commerce, the Federal Trade Commission, a European data protection authority, or any other US or European judicial or regulatory body upon their request.
7.1. Vendor shall, to the extent required by European Data Protection Legislation, provide Customer with reasonable assistance at Customer’s cost and expense with data protection impact assessments or prior consultations with data protection authorities that Customer is required to carry out under European Data Protection
Data Processing Agreement 5
Legislation in relation to Personal Data that is subject to European Data Protection Legislation.
8.1. Vendor shall, taking into account the nature of the processing, provide reasonable assistance to Customer insofar as this is possible and at Customer’s cost and expense, to enable Customer to respond to requests from a data subject seeking to exercise their rights under Applicable Data Protection Legislation. In the event that such a request is made directly to Vendor, if the Vendor can, through reasonable means, identify the Customer as to the controller of the Personal Data of a data subject, the Vendor shall promptly inform the Customer of the same.
9.1. Upon termination or expiry of this Agreement, Vendor will (at Customer’s election) delete or return to Customer all Customer Data (including copies) in its possession or control as soon as reasonably practicable and within a maximum period of 30 days of termination or expiry of the Agreement, save that this requirement will not apply to the extent that Vendor is required by the applicable law to retain some or all of the Customer Data, or to Customer Data it has archived on back-up systems, which Customer Data Vendor will securely isolate and protect from any further processing, except to the extent required by applicable law.
10.1. For purposes of this Section 11, the terms “business,” “commercial purpose,” “sell” and “service provider” have the meanings given in the CCPA, and “personal information” shall mean Personal Data that constitutes “personal information” governed by the CCPA.
10.2. It is the parties’ intent that with respect to any personal information, the Customer is a business and the Vendor is a service provider. Vendor shall not (a) sell any personal information; (b) retain, use or disclose any personal information for any purpose other than for the specific purpose of providing the Service, including retaining, using, or disclosing the personal information for a commercial purpose other than the provision of the Service; or (c) retain, use or disclose the personal information outside of the direct business relationship between the parties. The vendor hereby certifies that it understands its obligations under this Section 11 and will comply with them.
10.3. The parties acknowledge and agree that the Vendor’s provision of the Service encompasses, and that the parties’ business relationship contemplates, Vendor’s performance of its obligations and exercise of its rights under the Agreement.
11.1. This DPA contains certain terms required by the Vendor relating to data protection, privacy and security which has been updated to reflect certain requirements of Applicable Data Protection Legislation, where applicable. In the event (and to the extent only) of a conflict (whether actual or perceived) between the GDPR and the CCPA, the parties (or relevant party as the case may be) shall comply with the more onerous requirement or standard which shall, in the event of a dispute in that regard, be solely determined by Vendor.
11.2. Notwithstanding anything else to the contrary in the Agreement and without prejudice to Section 3.1, the Vendor reserves the right to make any modification to this DPA as may be required to comply with Applicable Data Protection Legislation.
11.3. Except as amended by this DPA, the Agreement will remain in full force and effect.
11.4. If there is a conflict between the Agreement and this DPA, the terms of this DPA will prevail.
11.5. Any claims brought under this DPA shall be subject to the terms and conditions, including but not limited to, the exclusions and limitations set forth in the Agreement.
11.6. Notwithstanding anything in the Agreement or any order form entered in connection therewith, the parties acknowledge and agree that Vendor access to Customer Data does not constitute part of the consideration exchanged by the parties in respect of the Agreement.
The Member States may complete or specify, according to their national procedures, any additional necessary information to be contained in this Appendix.
Data exporter
The data exporter is:
Data importer
The data importer is Secoda, Inc.
Nature of Services
The Nature of Services is set out in the Agreement which describes the provision of services to the Customer.
Categories of data subjects
Any data subjects contained in Data Exporter’s data being used in the services as set out in the Agreement which describes the provision of services to the Customer.
Categories of data processed
The personal data processed concern the following categories of data:
Special categories of data (if applicable)
NA
Processing operations
The processing operations are set out in the Agreement which describes the provision of services to the Customer.
During the Agreement Term, when processing Personal Data on behalf of Customer in connection with the Services, Vendor has implemented and shall maintain appropriate technical and organizational security measures for the processing of such data, including the measures specified in this Exhibit to the extent applicable to Vendor’s processing of Personal Data.
1. Intrusion Prevention.
Vendor implements and maintains a working network firewall to protect data accessible via the Internet and will keep all Customer Data protected by the firewall at all times.
The vendor maintains risks and keeps its systems and software up to date with the latest upgrades, updates, bug fixes, new versions and other modifications necessary to ensure the security of the Customer Data.
The vendor uses anti-malware software and keeps the anti-malware software up to date.
2. Security Awareness Training
a. The vendor requires annual security and privacy training for all employees with access to Customer Data.
3. Physical Access Control
a. Vendor’s services and data are hosted in AWS facilities in the USA and protected by AWS in accordance with their security protocols. The vendor also provides Customers host data in an AWS facility in Europe.
4. Logical Access Controls
The vendor assigns a unique ID to each employee and leverages an Identity
Provider to manage access to systems processing Customer Data.
All-access to systems processing Customer Data is protected by Multi-Factor Authentication (MFA).
Vendor restricts access to Customer Data to only those people with a “need-to- know” for a Permitted Purpose and following least privileges principles.
The vendor regularly reviews quarterly the list of people and systems with access to Customer Data and removes accounts upon the termination of employment or a change in job status that results in employees no longer requiring access to Customer Data.
Vendor mandates and ensures the use of system-enforced “strong passwords” in accordance with the best practices (described below) on all systems hosting, storing, processing, or that have or control access to Customer Data and will require that all passwords and access credentials are kept confidential and not shared among personnel.
Password best practices implemented by Vendor’s Identity Provider. Passwords must meet the following criteria:
contain at least 12 characters;
must contain lowercase and uppercase letters, numbers and a special character;
cannot be part of a vendor-provided list of common passwords
The vendor maintains and enforces “account lockout” by disabling accounts with access to Customer Data when an account exceeds more than ten (10) consecutive incorrect password attempts.
The vendor does not operate any internal corporate network. All access to Vendor resources is protected by strong passwords and MFA.
Vendor monitors their production systems and implements and maintains security controls and procedures designed to prevent, detect and respond to identified threats and risks.
Strict privacy controls exist in the application code that is designed to ensure data privacy and to prevent one customer from accessing another customer’s data (i.e., logical separation).
5. Human Resource Security
The vendor conducts at its expense a criminal background investigation on all employees who are to perform material aspects of the Services under this Agreement.
The vendor requires all employees to acknowledge in writing, at the time of hire, they will adhere to terms that are in accordance with Vendor’s security policy and to protect all Customer Data at all times. The vendor requires all employees to sign a confidentiality statement at the time of hire.
6. Disaster Recovery and Back-up Controls
All Customer Data is permanently stored in the same region in which the
Customer is located, and is backed up for disaster recovery.
The vendor relies on a reputable Infrastructure-As-A-Service provider. Vendor leverages their portfolio of globally redundant services to ensure Services run reliably. Vendor benefits from the ability to dynamically scale up, or completely re-provision its infrastructure resources on an as-needed basis, across multiple geographical areas, using the same vendor, tools, and APIs. The vendor’s infrastructure scales up and down on-demand as part of day-to-day operations and does so in response to any changes in our Customers’ needs. This includes not just compute resources, but storage and database resources, networking, security, and DNS. Every component in Vendor’s infrastructure is designed and built for high availability.
The vendor’s data security, high availability, and built-in redundancy are designed to ensure application availability and protect information from accidental loss or destruction. Service restoration is within commercially reasonable efforts and is performed in conjunction with AWS’ ability to provide adequate infrastructure at the prevailing failover location. All the Vendor recovery and resilience mechanisms are tested regularly and processes are updated as required.
The vendor has no direct reliance on specific office locations to sustain operations. All operational access to production resources can be exercised at any location on the Internet. The vendor leverages a range of best-of-breed technologies and other critical cloud tools to deliver uninterrupted remote work for all employees.
All Customer Data deleted by Vendor is deleted from datastores in accordance with the NIST Special Publication 800-88 Revision 1, Guidelines for Media Sanitation December 18, 2014 (available at http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-88r1.pdf)With respect to Customer Data encrypted in compliance with this security policy, this deletion may be done by permanently and securely deleting all copies of the keys used for encryption.
7. Business Continuity and Security Incident Response Plan
a. Vendor has implemented a formal procedure for handling security events. When security events are detected they are escalated to an emergency alias, relevant parties are paged, notified and assembled to rapidly address the event. After a security event is contained and mitigated, relevant teams write up a post- mortem analysis, which is reviewed in person and distributed across the company and includes action items that will make the detection and prevention of a similar event easier in the future.
8. Storage and Transmission Security
Customer data is stored in dedicated datastores.
All data sent to or from the Vendor is encrypted in transit using TLS 1.2.
Customer Personal Data is encrypted at rest using 256-bit encryption, leveraging current industry-standard technology.
All Vendor datastores used to process Customer data are configured and patched using commercially reasonable methods according to industry-recognized system-hardening standards.
9. Internal Audits
Vendor regularly tests their security systems and processes to ensure they meet the requirements of this security policy and ensures that the physical and environmental security controls are audited by an external party.
10. Secure Disposal
The vendor will permanently and securely delete all live (online or network accessible) instances of the Customer Data within 90 days upon the Customer’s in-app deletion request.
When required by law to retain archival copies of Customer Data for tax or similar regulatory purposes, this archived Customer Data is stored as a “cold” or offline (i.e., not available for immediate or interactive use) backup stored in a physically secure facility.
11. Risk Identification & Assessment
The vendor performs periodic (but no less than once per month) application
vulnerability scans. Vulnerabilities shall be remediated on a risk basis.
The vendor employs an independent third-party vendor to conduct periodic (but no less than once per year) penetration tests on their web properties.
12. Vendor & Services Providers
a. Prior to engaging new third-party service providers or vendors who will have access to Vendor Data, the Vendor conducts a risk assessment of vendors’ data security practices.
13. Change and Configuration Management
a. The vendor uses continuous automation for application and operating systems deployment for new releases. Integration testing and unit testing are done upon every build with safeguards in place for availability and reliability. The vendor has a process for critical emergency fixes that can be deployed to Customers within minutes. As such Vendors can roll out security updates as required based on criticality.
For the purposes of Article 26(2) of Directive 95/46/EC for the transfer of personal data to processors established in third countries which do not ensure an adequate level of data protection
Secoda, Inc. (hereinafter “data importer“) and [insert name of Customer] (hereinafter the “data exporter“) each a “party”; together “the parties”,
HAVE AGREED on the following Contractual Clauses (the Clauses) in order to adduce adequate safeguards with respect to the protection of privacy and fundamental rights and freedoms of individuals for the transfer by the data exporter to the data importer of the personal data specified in Annex 1.
Clause 1
Definitions
For the purposes of the Clauses:
1. ‘personal data’, ‘special categories of data, ‘process/processing‘, ‘controller‘, ‘processor‘, ‘data subject‘ and ‘supervisory authority shall have the same meaning as in Directive 95/46/EC of the European Parliament and of the Council of 24 October 1995 on the protection of individuals with regard to the processing of personal data and on the free movement of such data;
2. ‘the data exporter‘ means the controller who transfers the personal data;
‘the data importer‘ means the processor who agrees to receive from the data exporter personal data intended for processing on his behalf after the transfer in accordance with his instructions and the terms of the Clauses and who is not subject to a third country’s system ensuring adequate protection within the meaning of Article 25(1) of Directive 95/46/EC;
‘the subprocessor‘ means any processor engaged by the data importer or by any other subprocessor of the data importer who agrees to receive from the data importer or from any other subprocessor of the data importer personal data exclusively intended for processing activities to be carried out on behalf of the data exporter after the transfer in accordance with his instructions, the terms of the Clauses and the terms of the written subcontract;
‘the applicable data protection law‘ means the legislation protecting the fundamental rights and freedoms of individuals and, in particular, their right to privacy with respect to the processing of personal data applicable to a data controller in the Member State in which the data exporter is established;
‘technical and organizational security measures‘ means those measures aimed at protecting personal data against accidental or unlawful destruction or accidental loss, alteration, unauthorized disclosure or access, in particular where the processing involves the transmission of data over a network, and against all other unlawful forms of processing.
Clause 2
Details of the transfer
The details of the transfer and in particular the special categories of personal data where applicable are specified in Appendix 1 which forms an integral part of the Clauses.
Clause 3
Third-party beneficiary clause
The data subject can enforce against the data exporter this Clause, Clause 4(b) to (i), Clause 5(a) to (e), and (g) to (j), Clause 6(1) and (2), Clause 7, Clause 8(2), and Clauses 9 to 12 as a third-party beneficiary.
The data subject can enforce against the data importer this Clause, Clause 5(a) to (e) and (g), Clause 6, Clause 7, Clause 8(2), and Clauses 9 to 12, in cases where the data exporter has factually disappeared or has ceased to exist in law unless any successor entity has assumed the entire legal obligations of the data exporter by contract or by operation of law, as a result of which it takes on the rights and obligations of the data exporter, in which case the data subject can enforce them against such entity.
The data subject can enforce against the subprocessor this Clause, Clause 5(a) to (e) and (g), Clause 6, Clause 7, Clause 8(2), and Clauses 9 to 12, in cases where both the data exporter and the data importer have factually disappeared or ceased to exist in law or have become insolvent, unless any successor entity has assumed the entire legal obligations of the data exporter by contract or by operation of law as a result of which it takes on the rights and obligations of the data exporter, in whichcase the data subject can enforce them against such entity. Such third-party liability of the subprocessor shall be limited to its own processing operations under the Clauses.
The parties do not object to a data subject being represented by an association or other body if the data subject so expressly wishes and if permitted by national law.
Clause 4
Obligations of the data exporter
The data exporter agrees and warrants:
that the processing, including the transfer itself, of the personal data has been and will continue to be carried out in accordance with the relevant provisions of the applicable data protection law (and, where applicable, has been notified to the relevant authorities of the Member State where the data exporter is established) and does not violate the relevant provisions of that State;
that it has instructed and throughout the duration of the personal data processing services will instruct the data importer to process the personal data transferred only on the data exporter’s behalf and in accordance with the applicable data protection law and the Clauses;
that the data importer will provide sufficient guarantees in respect of the technical and organisational security measures specified in Appendix 2 to this contract;
that after assessment of the requirements of the applicable data protection law, the security measures are appropriate to protect personal data against accidental or unlawful destruction or accidental loss, alteration, unauthorised disclosure or access, in particular where the processing involves the transmission of data over a network, and against all other unlawful forms of processing, and that these measures ensure a level of security appropriate to the risks presented by the processing and the nature of the data to be protected having regard to the state of the art and the cost of their implementation;
that it will ensure compliance with the security measures;
that, if the transfer involves special categories of data, the data subject has been informed or will be informed before, or as soon as possible after, the transfer that its data could be transmitted to a third country not providing adequate protection within the meaning of Directive 95/46/EC;
to forward any notification received from the data importer or any subprocessor pursuant to Clause 5(b) and Clause 8(3) to the data protection supervisory authority if the data exporter decides to continue the transferor to lift the suspension;
to make available to the data subjects upon request a copy of the Clauses, with the exception of Appendix 2, and a summary description of the security measures, as well as a copy of any contract for subprocessing services which has to be made in accordance with the Clauses, unless the Clauses or the contract contain commercial information, in which case it may remove such commercial information;
that, in the event of subprocessing, the processing activity is carried out in accordance with Clause 11 by a subprocessor providing at least the same level of protection for the personal data and the rights of the data subject as the data importer under the Clauses; and
that it will ensure compliance with Clause 4(a) to (i).
Clause 5
Obligations of the data importer
The data importer agrees and warrants:
to process the personal data only on behalf of the data exporter and in compliance with its instructions and the Clauses; if it cannot provide such compliance for whatever reasons, it agrees to inform promptly the data exporter of its inability to comply, in which case the data exporter is entitled to suspend the transfer of data and/or terminate the contract;
that it has no reason to believe that the legislation applicable to it prevents it from fulfilling the instructions received from the data exporter and its obligations under the contract and that in the event of a change in this legislation which is likely to have a substantial adverse effect on the warranties and obligations provided by the Clauses, it will promptly notify the change to the data exporter as soon as it is aware, in which case the data exporter is entitled to suspend the transfer of data and/or terminate the contract;
that it has implemented the technical and organizational security measures specified in Appendix 2 before processing the personal data transferred;
that it will promptly notify the data exporter about:
any legally binding request for disclosure of the personal data by a law enforcement authority unless otherwise prohibited, such as a prohibition under criminal law to preserve the confidentiality of a law enforcement investigation,
any accidental or unauthorized access, and
any request received directly from the data subjects without responding to that request unless it has been otherwise authorized to do so;
to deal promptly and properly with all inquiries from the data exporter relating to its processing of the personal data subject to the transfer and to abide by the advice of the supervisory authority with regard to the processing of the data transferred;
at the request of the data, exporter to submit its data processing facilities for an audit of the processing activities covered by the Clauses which shall be carried out by the data exporter or an inspection body composed of independent members and in possession of the required professional qualifications bound by a duty of confidentiality, selected by the data exporter, where applicable, in agreement with the supervisory authority;
to make available to the data subject upon request a copy of the Clauses, or any existing contract for sub-processing, unless the Clauses or contract contain commercial information, in which case it may remove such commercial information, with the exception of Appendix 2 which shall be replaced by a summary description of the security measures in those cases where the data subject is unable to obtain a copy from the data exporter;
that, in the event of subprocessing, it has previously informed the data exporter and obtained its prior written consent;
that the processing services by the subprocessor will be carried out in accordance with Clause 11;
to send promptly a copy of any subprocessor agreement it concludes under the Clauses to the data exporter.
Clause 6
Liability
1. The parties agree that any data subject, who has suffered damage as a result of any breach of the obligations referred to in Clause 3 or in Clause 11 by any party or subprocessor is entitled to receive compensation from the data exporter for the damage suffered.
2. If a data subject is not able to bring a claim for compensation in accordance with paragraph 1 against the data exporter, arising out of a breach by the data importer or his subprocessor of any of their obligations referred to in Clause 3 or in Clause 11, because the data exporter has factually disappeared or ceased to exist in law or has become insolvent, the data importer agrees that the data subject may issue a claim against the data importer as if it were the data exporter, unless any successor entity has assumed the entire legal obligations of the data exporter by the contract or by operation of law, in which case the data subject can enforce its rights against such entity.
The data importer may not rely on a breach by a subprocessor of its obligations in order to avoid its own liabilities.
1. If a data subject is not able to bring a claim against the data exporter or the data importer referred to in paragraphs 1 and 2, arising out of a breach by the subprocessor of any of their obligations referred to in Clause 3 or in Clause 11 because both the data exporter and the data importer have factually disappeared or ceased to exist in law or have become insolvent, the subprocessor agrees that the data subject may issue a claim against the data subprocessor with regard to its own processing operations under the Clauses as if it were the data exporter or the data importer, unless any successor entity has assumed the entire legal obligations of the data exporter or data importer by contract or by operation of law, in which case the data subject can enforce its rights against such entity. The liability of the subprocessor shall be limited to its own processing operations under the Clauses.
Clause 7
Mediation and jurisdiction
1. The data importer agrees that if the data subject invokes against it third-party beneficiary rights and/or claims compensation for damages under the Clauses, the data importer will accept the decision of the data subject:
a. to refer the dispute to mediation, by an independent person or, where applicable, by the supervisory authority;
b. to refer the dispute to the courts in the Member State in which the data exporter is established.
2. The parties agree that the choice made by the data subject will not prejudice its substantive or procedural rights to seek remedies in accordance with other provisions of national or international law.
Clause 8
Cooperation with supervisory authorities
The data exporter agrees to deposit a copy of this contract with the supervisory authority if it so requests or if such deposit is required under the applicable data protection law.
The parties agree that the supervisory authority has the right to conduct an audit of the data importer, and of any subprocessor, which has the same scope and is subject to the same conditions as would apply to an audit of the data exporter under the applicable data protection law.
The data importer shall promptly inform the data exporter about the existence of legislation applicable to it or any subprocessor preventing the conduct of an audit of the data importer, or any subprocessor, pursuant to paragraph 2. In such a case the data exporter shall be entitled to take the measures foreseen in Clause 5 (b).
Clause 9
Governing Law
The Clauses shall be governed by the law of the Member State in which the data exporter is established.
Clause 10
Variation of the contract
The parties undertake not to vary or modify the Clauses. This does not preclude the parties from adding clauses on business-related issues where required as long as they do not contradict the Clause.
Clause 11
Subprocessing
The data importer shall not subcontract any of its processing operations performed on behalf of the data exporter under the Clauses without the prior written consent of the data exporter. Where the data importer subcontracts its obligations under the Clauses, with the consent of the data exporter, it shall do so only by way of a written agreement with the subprocessor which imposes the same obligations on the subprocessor as are imposed on the data importer under the Clauses. Where the subprocessor fails to fulfil its data protection obligations under such written agreement the data importer shall remain fully liable to the data exporter for the performance of the subprocessor’s obligations under such agreement.
The prior written contract between the data importer and the subprocessor shall also provide for a third-party beneficiary clause as laid down in Clause 3 for cases where the data subject is not able to bring the claim for compensation referred to in paragraph 1 of Clause 6 against the data exporter or the data importer because they have factually disappeared or have ceased to exist in law or have become insolvent and no successor entity has assumed the entire legal obligations of the data exporter or data importer by contract or by operation of law. Such third-party liability of the subprocessor shall be limited to its own processing operations under the Clauses.
The provisions relating to data protection aspects for subprocessing of the contract referred to in paragraph 1 shall be governed by the law of the Member State in which the data exporter is established.
The data exporter shall keep a list of sub-processing agreements concluded under the Clauses and notified by the data importer pursuant to Clause 5 (j), which shall be updated at least once a year. The list shall be available to the data exporter’s data protection supervisory authority. 3
Clause 12
Obligation after the termination of personal data processing services
1. The parties agree that on the termination of the provision of data processing services, the data importer and the subprocessor shall, at the choice of the data exporter, return all the personal data transferred and the copies thereof to the data exporter or shall destroy all the personal data and certify to the data exporter that it has done so, unless legislation imposed upon the data importer prevents it from returning or destroying all or part of the personal data transferred. In that case, the
data importer warrants that it will guarantee the confidentiality of the personal data transferred and will not actively process the personal data transferred anymore.
2. The data importer and the subprocessor warrant that upon request of the data exporter and/or of the supervisory authority, it will submit its data processing facilities for an audit of the measures referred to in paragraph
Appendix 1 to the Standard Contractual Clauses
The details of the transfer are specified in Exhibit A of the DPA.
Appendix 2 to the Standard Contractual Clauses
Description of the technical and organizational security measures implemented by the data importer in accordance with Clauses 4(d) and 5(c):
The technical and organizational security measures implemented by the data importer are as described in Exhibit B of the DPA.
Appendix 3 to the Standard Contractual Clauses
The parties acknowledge that Clause 10 of the Clauses permits them to include additional business-related terms provided they do not contradict with the Clauses. Accordingly, this Appendix sets out the parties’ interpretation of their respective obligations under specific Clauses identified below.
Where a party complies with the commercial interpretations set out in this Appendix, that party shall be deemed by the other party to have complied with its commitments under the Clauses. However, it is not the intention of either party that the commercial clauses below will have the effect of contradicting the Clauses.
For the purposes of this Appendix, “DPA” means the Data Processing Addendum in place between data importer and data exporter and to which these Clauses are incorporated and “Agreement” shall have the meaning given to it in the DPA.
Clause 4(h) and 8: Disclosure of these Clauses
1. The data exporter agrees that these Clauses constitute data importer’s Confidential Information as that term is defined in the Agreement and may not be disclosed by the data exporter to any third party without data importer’s prior written consent unless permitted by the Agreement. This shall not prevent disclosure of these Clauses to a data subject pursuant to Clause 4(h) or a supervisory authority pursuant to Clause 8.
Clause 5(a) and 5(b): Suspension of data transfers and termination:
The parties acknowledge that for the purposes of Clause 5(a), the data importer may process the personal data only on behalf of the data exporter and in compliance with its documented instructions as provided by the data exporter in the DPA and these Clauses.
The parties acknowledge that if the data importer cannot, for whatever reason, provide compliance with Clause 5(a) and/or Clause 5(b), the data importer agrees to promptly inform the data exporter of its inability to comply, in which case the data exporter is entitled to suspend the transfer of data and/or terminate the affected part of the Services.
If the data exporter intends to suspend the transfer of personal data and/or terminate the affected part of the Services, it shall endeavour to first provide notice to the data importer and provide data importer with a reasonable period of time to cure the non-compliance (“Cure Period”). In addition, the data exporter and data importer shall reasonably cooperate with each other during the Cure Period to agree on what additional safeguards or other measures, if any, may be reasonably required to ensure the data importer’s compliance with the Clauses and data exporter’s compliance with applicable data protection law, in accordance with Section 3.4 of the DPA.
If after the Cure Period the data importer has not or cannot cure the non-compliance in accordance with paragraph (4) above then the data exporter may suspend and/or terminate the affected part of the Services in accordance with the provisions of the Agreement without liability to either party (but without prejudice to any fees incurred by the data exporter prior to suspension or termination).
Clause 5(f): Audit:
1. Data exporter acknowledges and agrees that it exercises its audit right under Clause 5(f) by instructing data importer to comply with the audit measures described in Clause 8 (Audits) of the DPA.
Clause 5(j): Disclosure of subprocessor agreements
1. The parties acknowledge the obligation of the data importer to send promptly a copy of any onward subprocessor agreement it concludes under the Clauses to the data exporter.
The parties further acknowledge that, pursuant to subprocessor confidentiality restrictions, data importers may be restricted from disclosing onward subprocessor agreements to the data exporters. Notwithstanding this, the data importer shall use reasonable efforts to require any subprocessor it appoints to permit it to disclose the subprocessor agreement to the data exporter.
Even where the data importer cannot disclose a subprocessor agreement to data exporter, the parties agree that, upon the request of data exporter, data importer shall (on a confidential basis) provide all information it reasonably in connection with such sub-processing agreement to the data exporter.
Clause 6: Liability
1. Any claims brought under or in connection with the Clauses shall be subject to the terms and conditions, including but not limited to, the exclusions and limitations of liability set forth in the Agreement. In no event shall any party limit its liability with respect to any data subject rights under these Clauses.
Clause 11: Onward subprocessing
The parties acknowledge that, pursuant to FAQ II.1 in Article 29 Working Party Paper WP 176 entitled “FAQs in order to address some issues raised by the entry into force of the EU Commission Decision 2010/87/EU of 5 February 2010 on standard contractual clauses for the transfer of personal data to processors established in third countries under Directive 95/46/EC” the data exporter may provide a general consent to onward sub processing by the data importer.
Accordingly, data exporter provides a general consent to data importer, pursuant to Clause 11 of these Clauses, to engage onward subprocessors. Such consent is conditional on the data importer’s compliance with the requirements set out in Clause 5 (Subprocessing) of the DPA.



Seda's terms of use policy
Thank you for visiting Seda the data platform which helps teams find data faster
In these Terms, we or us means Secoda Technologies Ltd. We provide Seda or Secoda, a data discovery tool that helps users find, understand and use data to make decisions, which we provide through our website at seda.ai (the Site) or Secoda.co. These Terms set out the terms and conditions on which we make our Site available, and on which we make Secoda and Seda available to registered users. By using the Site, Secoda or Seda you agree to these Terms.
Full details are set out in the relevant sections of these Terms below, but keeping it brief:
We will make Seda available to you based on the subscription model you’ve chosen;
We rely on you to make sure that any authentication method you use to log into Seda remains secure;
Any data related to your account Seda (which we defined as Your Content) is yours. We don’t own any of it, we don’t control it, we don’t use it for our own purposes and we don’t even look at it unless you need us to in connection with a support query. If you close your account, Your Content will automatically be deleted.
You must not use Seda for any unlawful purpose, and must ensure that if you upload or share Your Content you do so lawfully (and in particular without breaching applicable law, anyone else’s rights, or any applicable licence terms);
You can close your account whenever you like, but pre-paid subscription fees are not refundable;
Other relevant pages you might want to look at are:
Our privacy policy, which describes how we make use of personal data received from users of our Site, and also explains our use of cookies; and
Registration. You can register as a user of Seda here. To register (and to log in) you will need to create a user account, which will be authenticated either through email (we will send you an email containing a one-time code allowing you to log in) or through the credentials associated with a third-party account (such as your Google account, or any other forms of authentication we might build into Secoda or Seda from time to time). User accounts can be assigned different roles (the highest being the Workspace Owner, who will be responsible for payment as well as ownership of the relevant Workspace within Secoda or Seda). Different user roles will have different permissions in relation to the metadata on Secoda or Seda and access to different features.
Security. You should keep your account (and any third-party account you use to authenticate, or receive credentials for, your access to Seda) secure, and not allow anyone else to use your account. If any activity takes place on your account, or any content is uploaded through your account, then you are responsible for it. You must let us know immediately if you discover or suspect that someone else has accessed your account.
Payment. You must pay the applicable subscription fee (if any) in advance, subject to any credits which we may have applied to your account. You can make payment by following the instructions on the Site. We do not collect or process your credit or debit card details when you make payments through the Site, but these will be received by our payment processing service providers.
Changes to our subscription model. We may withdraw or change any subscription model and/or price at any time. This will not affect any subscription that you have already paid for. We will inform you of any changes so that you can choose whether or not to cancel your subscription before it next renews.
Our obligations. We will make Seda available to you in accordance with these Terms, and incorporating the product features described on our Site.
Your obligations. When you use Seda:
You confirm that you are authorised to enter into a contract with us on these Terms, and to conduct any activities which you may conduct through your account. This means in particular that if you are an individual you are over eighteen years old and that if you are opening an account on behalf of a company or other business you are authorised by that business to act on its behalf;
You may only use Seda for lawful purposes. You may not use it in any way that breaches any local or international law, for the purposes of fraud, or to transmit unsolicited advertising or spam;
Any information you submit at any time (whether registering for an account with us or otherwise) must be true and not misleading;
You must not misuse Seda or our Site by introducing viruses or other malicious code to them or to our systems, nor try to gain unauthorised access to them, to any related systems or servers or to any related source code. You must not attack Secoda or Seda through DDOS or otherwise. As you probably know, breaching this provision would be a criminal act, which may oblige us to report you to law enforcement and provide them with such information as we may have about you;
You must use our Site honestly. For example, you should not impersonate anyone else, misrepresent your affiliation with any entity, and
You must not use any bots or other programs to crawl or scrape data from Seda or our Site.
Rights in our content. The intellectual property rights in all of the content on and in our Site belong either to us or to whomever licensed that content to us. You may not copy or make any use of that content without having first obtained our permission or permission from whomever owns the relevant intellectual property rights. Uses which are expressly permitted by law are however allowed. If you would like to make any use of any of our content then please contact us and we can discuss this with you.
No assignment of Intellectual Property Rights: You retains your Intellectual Property Rights and nothing in this Agreement will be deemed as a transfer, license or sharing of such Intellectual Property Rights.
Metric data: We may monitor the use of Seda using metric tools in order to provide us with insights into the user experience. For example, we might monitor which Seda features are being used by particular organisations or users, how often particular users are active, whether users are completing or dropping from particular flows (like sign-up or configuration flows), how long it takes users to adopt new features or how quickly features are abandoned. All arising metric data will belong to us. To be clear: this monitoring activity will never involve us seeing any of Your Content. For example: our metric data might tell us that a user has used the description feature, which helps us know how often those features are used, but it will not show us the contents of the table.
Termination by you. You may terminate any contract between you and us on the Terms and close your account by written notice to us at any time. You should note that termination of your contract with us will not entitle you to any refund of any prepaid fees.
Termination by us. If you are in breach of the Terms, we may take any of the following actions:
Issuing you with a written warning specifying the breach and requiring its remedy;
Suspension or permanent withdrawal of your account and your use of Seda;
Termination of any contract between you and us on the Terms;
Taking legal action against you; or
Disclosing your personal information to law enforcement authorities.
We also reserve the right to terminate any contract between you and us, and/or suspend or terminate your account, by written notice to you at any time. We will try to give you reasonable notice, and ensure that an appropriate proportion of any prepaid fees are returned where we have terminated without cause. However, nothing in our relationship with you guarantees your continued use of Seda.
Effect of Termination. Termination of the contract between you and us will not affect any rights or remedies of the parties in existence at the time of termination. For instance, if at the time of termination one of us owes the other any sums, then they will still be owed. Any of the Terms which expressly or impliedly survive termination will continue in force.
We provide a platform for data collaboration. Because our role is limited, and we don’t control the use of our platform or the value of data shared, we limit and exclude our liability to an appropriate degree. This section explains the ways in which our liability to you is limited and excluded.
Where we don’t limit or exclude our liability. We do not limit or exclude our liability for anything for which we cannot lawfully limit or exclude our liability. For example, we do not limit our liability for death or personal injury caused by our negligence, or for fraud. This statement takes priority over the rest of the Terms.
No implied terms. We provide access to the Site and to Seda on these Terms alone. To the fullest extent permitted by law, we expressly exclude any and all conditions, warranties and other terms which might otherwise be implied by statute, under common law, or otherwise.
We’re at the mercy of the Internet. You understand that there is some inherent instability in communications networks and that we may need to take down or maintain our Site from time to time. You accept that access to our Site is permitted on a temporary basis and we will not be liable if it is unavailable for any reason. At the same time, the Site and Seda are provided “as is” and without any warranty. For example, while obviously we do our best to correct defects, we do not warrant that either will be uninterrupted, free from errors, or free from viruses or malicious code.
No indirect or consequential loss. We expressly exclude any liability for any indirect or consequential loss, damage, costs or expenses incurred or suffered by you in connection with your use of our Site. We are not liable for losses, damages, costs and expenses that are not foreseeable to both you and us at the time you open your account with us or which are not caused by our breach.
No liability for certain kinds of loss. We expressly exclude any liability for any loss, damage, costs or expenses incurred or suffered by you (in each case whether direct or indirect) if that liability comes within one of the following categories: loss of business, loss of revenue, loss of contract, loss of reputation, or loss of profit. In short, we are not liable for business losses.
Cap on liability. Our total aggregate liability to you in connection with your use of Seda will be limited in all circumstances (whether arising in negligence, including tort, breach of contract or otherwise) to a maximum sum equal to five times the Fees derived by us from your use of our Site during the twelve (12) months prior to the event giving rise to our liability.
Notwithstanding the foregoing, we will remain liable without contractual limitation for your damages: (i) which are based on our intentional or gross negligence (ii) breach of our duty or on an intentional or grossly negligent breach of duty by our legal representative or our vicarious agents (iii) which are based on our violation of Data Protection Law obligations (iv) which are based on violation of our confidentiality obligations (v) which are based on our violation of third party Intellectual Property Rights.
If we are subject to any third-party claim as a result of your breach of any of your obligations under the Terms, or as a result of your negligence, misrepresentation or other wrongful act, then you will indemnify us against that claim. Indemnifying us means you will indemnify us and hold us harmless against all direct costs, expenses, losses, damages or liabilities suffered or incurred by us as a result of or in connection with that third-party claim, including (without limitation) any reasonable legal and professional fees. You also agree to provide us with all reasonable assistance and information we may request from you in order to enable us to defend and settle the claim and mitigate our (and your) liability.
Linking to our Site. You can link to our Site provided that you do so in a way that is fair and legal. You may not link to our Site in order to damage or take advantage of our reputation or to suggest any false form of association, endorsement or relationship between you and us. You may not “hotlink” to our Site or to any content on it, nor embed or frame any part of our Site or any such content on any other site. If we ask you to stop linking to our Site then you must do so immediately.
Third party links. Our Site contains links to various third party sites and resources. We have no control, and are not responsible for, any data, content or services provided by third parties.
We may revise these Terms at any time. You should check our Terms for changes from time to time, but if the revisions are material then we will notify you of them using the contact details you have provided to us or by messaging your account. By continuing to use our Site or Seda you will be accepting our revised Terms.
Affliates: All use by your affiliates is permitted. You may use Seda for the benefit of your Affiliates to the extent that you are permitted to use the Seda under this Agreement. An Affiliate may also independently use Seda or purchase services under this Agreement. You may authorize one or more third-party service providers to access and use Seda to the extent of your permitted use under this Agreement, but solely on your behalf and solely to support your internal business operations.
Invoices: All invoices due under this Agreement shall be copied to: [email protected], whichever is applicable, before any payment deadline can validly commence.
Severance. If any court or competent authority determines that any provision or partprovision of the Terms is invalid, unlawful or unenforceable then that provision or partprovision will be severed from the rest of the Terms, which will continue in full force.
Entire agreement. The Terms constitute the entire agreement between you and us relating to your use of the Site and Seda. You acknowledge that you have not entered into any contract with us on the basis of any representation or warranty that is not set out expressly in the Terms.
Waivers. Our failure to enforce any provision of the Terms will not constitute a waiver of your breach of that provision.
Assignment. Any contract between you and us made on the Terms is personal to you, and you may not assign, transfer, sub-contract or otherwise deal in any of your rights and responsibilities under the Terms.
Third Party Rights. A person who is not a party to any contract under these Terms shall not have any rights to enforce any of them.
Governing law. The Terms and any contract between you and us on the Terms are governed by the laws of Ontario and Canada.
Disputes. If any dispute arises between you and us in connection with your use of our
Site or Seda, then you and we will attempt to resolve that dispute through discussion. If we are unable to resolve the dispute by discussion, then the courts of Ontario will have exclusive jurisdiction over any claim. If you are not resident in Ontario then we reserve the right to bring proceedings against you in any court in your country of residence.
If you have any questions, comments or requests regarding the Terms or any concerns about any material featured on our Site, please contact us at [email protected] or use the “contact us” form or button on our Site.
Last updated 23.12.2021
Subscriptions and renewal. We offer access to Seda on the basis of fixed-term subscriptions, priced on the basis of team size, data resources and any additional features such as additional integrations. Further information is available on our pricing page. . If you do not wish to renew your subscription with us, you must notify us prior to the renewal date.